
Access the webinar recording to learn how to stop AI-powered synthetic identities without slowing onboarding.

Gain insight on the latest cyber threat activities and how to prevent them.






NORWALK, CT, September 15, 2025 –SDG, a global provider of AI-driven identity, threat, and risk management solutions, today announced its acquisition of Hub City Media, Inc. (HCM), a consultancy specializing…

Gain insight on the latest cyber threat activities and how to prevent them.




What’s more expensive than a data breach? A data breach without artificial intelligence. For years, the narrative around cybersecurity has been one of grim inevitability. A constant, costly, and exhausting…

In software development, a single action, such as an “install” click, can have significant security implications. In April, SDG issued a warning: as AI development and the ecosystem of coding…


Gain insight on the latest cyber threat activities and how to prevent them.





Gain insight on the latest cyber threat activities and how to prevent them.


Autonomous AI agents now operate in finance, healthcare, technology, and government, executing tasks with increasing independence and authority. These agents can orchestrate data processing, trigger transactions, or even make policy…


Gain insight on the latest cyber threat activities and how to prevent them.

Herndon, VA, June 12, 2025 — Strivacity, a recognized leader in customer identity and access management (CIAM), and SDG Corporation, a premier provider of cybersecurity advisory, transformation, and managed services,…

Access the webinar recording to stay ahead of evolving threats and protect your development lifecycle from end to end.

Microsoft licensing now makes up a significant portion of enterprise software spend. Yet many organizations continue to operate with a licensing footprint that is harder to govern than necessary. While…


Read this service brief and unlock the power of secure cloud service. Flexibility, scalability, and cost-effectiveness.

As Director of Risk, Compliance, and Information Security at SDG Corporation, Meetali oversees corporate governance and GRC practices across global operations. She recently sat down with Digitaltech Media to discuss…

They don’t clock in, take vacations, or fill out HR forms—but non-human identities (NHIs) are everywhere in your digital environment. Bots, APIs, service accounts, machine identities—they’re running automation, managing integrations,…


Gain insight on the latest cyber threat activities and how to prevent them.

Credential stuffing is an automated attack where threat actors use stolen username-password pairs from previous breaches to gain unauthorized access to accounts on other platforms. Since many users reuse passwords,…

Gain insight on the latest cyber threat activities and how to prevent them.

Access the webinar recording to stay ahead of evolving threats and protect your development lifecycle from end to end.

Generative AI is reshaping how organizations operate, empowering teams with tools that enhance creativity, efficiency, and scalability. Yet, amidst rapid technological advancements, a vital question remains: how can we ensure…


Author: Spencer Crane, Vice President of Product, ID Dataweb As someone who has helped healthcare organizations strengthen their security posture, I can tell you firsthand how quickly identity-driven threats have…

The U.S. Securities and Exchange Commission (SEC) has placed cybersecurity and operational resilience at the forefront of its 2025 examination priorities, emphasizing the increasing risks of cyber threats, data breaches,…

Identity is arguably one of the most critical aspects of a security infrastructure. Identity controls access to most interactions with online resources, including websites, applications, and network infrastructure. As identity…

Gain insight on the latest cyber threat activities and how to prevent them.

Identity Security Posture Management, or ISPM, provides organizations with a mechanism to manage and monitor security systems. As identity continues to become the main threat leveraged by bad actors, identity-related…

SEC Targets AI Misrepresentation The Department of Justice (DOJ) recently secured a guilty plea from Mina Tadrus, founder of Tadrus Capital LLC, for investment fraud. His hedge fund falsely claimed…

As organizations transition to passwordless authentication, they unlock numerous security and operational benefits. However, implementing this technology comes with its own set of challenges that must be strategically addressed to…


Gain insight on the latest cyber threat activities and how to prevent them.



As healthcare enters 2025, the industry faces an escalating cybersecurity crisis. Cyberattacks are becoming more frequent and sophisticated, preying on the sector’s heavy reliance on interconnected systems and vast amounts…


The start of 2025 is a good time to pause and reflect on 2024’s cybersecurity journey. It has been a year of significant challenges, hard-won lessons, and remarkable innovations. From…

Gain insight on the latest cyber threat activities and how to prevent them.

Gain insight on the latest cyber threat activities and how to prevent them.

Gain insight on the latest cyber threat activities and how to prevent them.



Gain insight on the latest cyber threat activities and how to prevent them.

By leveraging the powerful TruOps platform and integrating Panorays’ comprehensive cyber risk data and alerts, SDG provides a seamless combination of people, processes, and technology. Learn More.


Gain insight on the latest cyber threat activities and how to prevent them.

The threat of cyberattacks, especially ransomware, is more real than ever. Organizations need more than just traditional defenses to combat these threats—they need a strategy that can adapt and respond…

Many organizations depend heavily on Microsoft Active Directory (AD) as an integral part of their IT infrastructure since it allows identity and access management, authentication and authorization services. Learn More.

Gain insight on the latest cyber threat activities and how to prevent them.

Enterprise-level third-party risk management is a critical security priority for organizations that rely on third-party suppliers, vendors, contractors, and even nonhumans to succeed. Learn More.

Gain insight on the latest cyber threat activities and how to prevent them.

SDG’s Microsoft Managed Services offer a complete package tailored to your organization’s unique environment. Our services are flexible and adaptive, expanding as your organization grows to ensure protection from threats….

Gain insight on the latest cyber threat activities and how to prevent them.

Gain insight on the latest cyber threat activities and how to prevent them.

Florida’s new law requires organizations to adopt and maintain strong cybersecurity frameworks, like NIST CSF, ISO 27001/2, HITRUST, SOC 1/2, CIS 18 Controls. Learn more.


Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them

In the ever-evolving landscape of hedge funds, where data is the lifeblood of operations and a key component of competitive advantage, it is imperative to safeguard the confidentiality, integrity, and…

Cyberattacks in any form must be avoided—which means organizations need to have safeguards in place to protect from both direct and indirect consequences.

Mindful businesses would be wise to be aware of the rising DDoS threats, know the vulnerabilities in their own systems, and have ready a plan of response.
Mindful businesses would be wise to be take the critical steps needed to effectively evade ransomware and its aftermath.

The new SEC compliance regulations require organizations to have processes to assess, identify, and manage cybersecurity risks.

Organizations must achieve a 360-degree view of risk to prevent a ransomware attack. Establishing these prevention and recovery plans is critical.

AWS is the current leader in the cloud computing space, and with this leadership position comes great risk.

The NetWitness “network-forward” approach allows SDG to search, correlate, and analyze the ever-increasing volumes of data generated by modern organizations. Learn more.

Read this service brief and unlock the power of secure cloud service. Flexibility, scalability, and cost-effectiveness.

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them

The latest revision of ISO 27001, released on October 25, 2022, introduces several changes that aim to address evolving security challenges and ensure that information security management systems (ISMS) are…

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them

The cybersecurity domain is witnessing a new wave of transformation akin to the early 2000s/SOX era, once again driven by regulatory changes and evolving risk landscapes. From stringent SEC cybersecurity…

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them

As we step into the next chapter of technological evolution, the role of cloud computing continues to expand and redefine the landscape of IT infrastructure. 2024 promises to be a…

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them
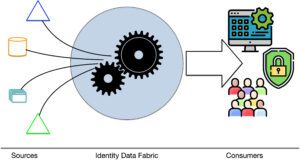
The sprawl of information across multiple repositories has complicated managing identity data. The addition of an Identity Data Fabric enables organizations to create a centralized view of identity data for…

SDG Corporation and Authomize Collaborate to Stop the Threat of Identity-Based Breaches NORWALK, CT – October 25, 2023: SDG, a global provider of cybersecurity, identity, risk, compliance, and cloud…

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them

The healthcare sector is ensnared in a relentless vortex of risk and regulation amid unanticipated disruptions and transformations. Navigating through this dynamic environment, healthcare entities grapple with a myriad of…

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them

Development, Security, and Operations (DevSecOps) enablement is the process of integrating security practices into the Development and Operations (DevOps) workflow. It aims to shift security considerations and responsibilities to earlier…

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them

BOSTON, MA – August 1, 2023 – SDG, a global provider of cybersecurity, identity, risk, compliance, and cloud security technology, consulting, and managed services, today announced a new partnership with…

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them

Gain Insight on the Latest Cyber Threat Activities and How to Prevent Them